Some technical guidance on hosted services in the Cloud and how they provide value
For those who are new to cloud solutions and the latest way to manage and secure your data assets, here are a few short briefing articles that may help your appreciation of the applications and benefits. We hope you find this information useful and welcome your feedback or requests for any additional articals.
OUTSOURCING IT TO THE CLOUD
A brief explanation
For all types of business, outsourcing IT to the Cloud can really help drive success.
As a result of the latest technology in computing, power supply and temperature control used by high end data centres, Cloud hosted services providing application and data services are now extremely reliable, highly available, performance optimised and efficient. For the business user the Cloud model is extremely appealing offering reduced capital and operational expenditure; by using cloud services the need for on site technical resources is virtually removed. Even with all these benefits, many companies are still unsure what the Cloud is, perhaps because it is a rather vague term that describes a service comprised of many different technologies and providing a wide range of solutions.
To understand the fundamentals, think of the Cloud as 3 services consisting of the following elements:-
܀ IaaS - "Infrastructure as a Service"
The racks, servers, power and cooling providing your hardware layer.
(Virtual & Physical Server Plaforms)
܀ PaaS - "Platform as a Service"
The server side operating systems & applications for your business.
܀ SaaS - "Software as a Service"
The client / desktop applications used by your business.
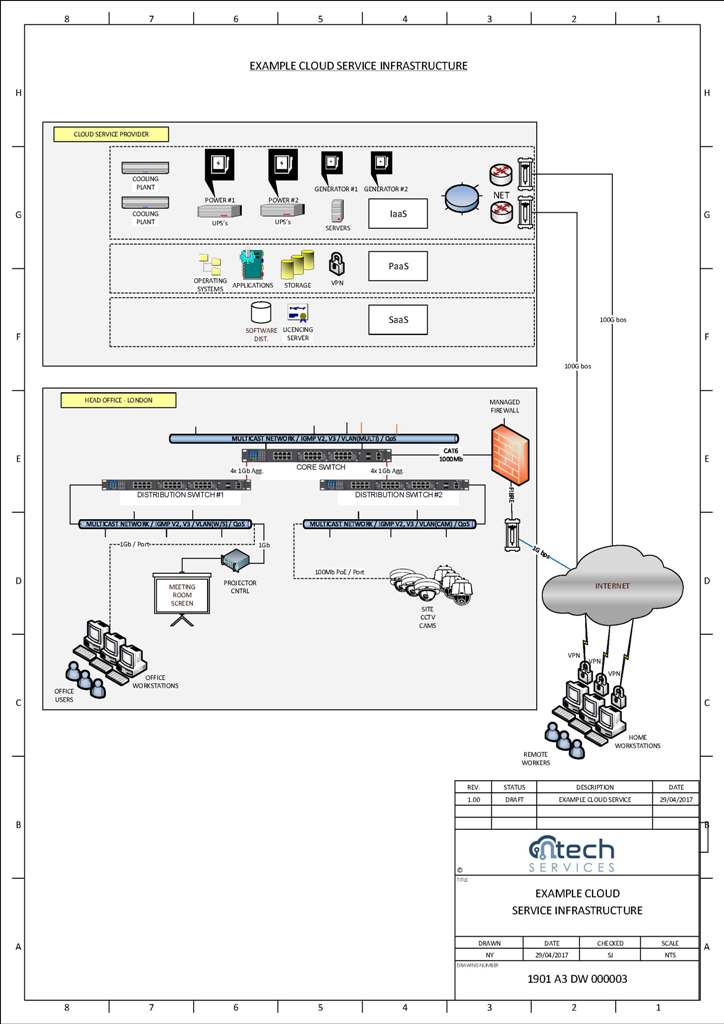
The first element of Cloud service is IaaS delivering hosted hardware which can be physical or virtual, computers, CPUs, and storage platforms. Instead of your servers being physically based in an office, employees access their data via the internet. For small and medium sized businesses, IaaS is often used to provide virtual servers that can act as a server on your network, but without the capital expense associated with the procurement or ongoing hardware maintenance and running costs. In addition IaaS includes the supply of Power (Grid supplied Mains, Uninteruptable Power Supply using batteries and Backup Generation), Temperature Management (Air Conditioning), and Secure Space (Physically controlled space with managment staff) for all your hosted service elements.
The second element of Cloud service is PaaS which provides remotely hosted server side software such as the server OS, file serving, database, email, data-collaboration, intranet and critical backup functions to name a few. This server side PaaS may either provisioned via virtual or physical machine(s) which can be easily scaled to meet changing business requirements. The main advantage of PaaS is the reduction in ongoing software maintenance and the associated staff needed to support the soft infrastructure resulting in significantly reduced operational costs.
The third element of Cloud service SaaS is the provision of end user applications usually deployed on one or more workstations and/or desktops/laptops via a software distribution and licencing platform. An example of SaaS is Microsoft Office 365 which is purchased on an ongoing contract rather than as an outright licence such as Microsoft Office 2019 Professional. Many large software companies have adopted this approach including AutoDesk and Adobe from whom you can either purchase software outright or as a service. Other examples of SaaS is via a Web Service where the application is hosted in the Cloud and is available to authorised users via the Internet. Web Service SaaS examples include helpdesk software, CCTV and customer relationship tools to name a few.
CLOUD SOLUTIONS SUMMARY
Compelling Business Reasons to Switch
So what are the true business gains offered by using the Cloud ?
In most cases this method of purchasing technology services for a business is significantly more tax efficient with the additional benefit of retaining a higher proportion of working capital available for ongoing operational purposes. As indicated above, there are little or no office costs associated with running the IT services for the business meaning no Servers, UPS's, Generators, Racks, Specialised Cooling Plant, Dedicated Rooms and the associated Technical Staff to maintain these. Furthermore, by migrating your IT functions to the Cloud it is easy to change office location, provide optimal home worker services, scale up or down or switch on or off an IT function entirely. Beyond the clear financial and operational benefits, another great reason to switch is to provide your business the opportunity to fully focus on its core objectives and deliverables.
ENDPOINT SECURITY
How does that protect my business?
Even with the best security available on your servers and in the Cloud users can be duped into executing malicious code.
In todays online world cyber crime is becoming an increasing threat to individuals, businesses and supporting systems. Even with the very best Firewall and Content Control technologies, due to the functionality built into email and web client software there is always a potential for new exploit code to be executed on the end users computer or mobile device. Although it is possible to prevent the execution of client site code such as Java often this is not practical as some legitimate services require these features. Therefore as a final line of defence it is recommended that an end point protection layer is added to all the client computers and mobile devices used to access company data. This means the installation of an anti-virus, anti-malware client machine application which can be managed or unmanaged. We recommend you choose a managed solution where we can undertake this IT task for you and monitor the status and health of your end points.
Managed End Point Security is delivered via SaaS where either the customer IT administrator and/or Ntech monitor the end points in your business. If you would like to see how we can assist with an end point security solution for your business, please visit our solutions page for more information.
The package of software which makes up an End Point Security solution may be boken down into three main functional components.
End Point Security Components:



1. The Management Platform that provides the functions of software licencing, security software deployment, monitoring of the end point computer updates and definitions and reporting.
2. The End Point Software which is deployed and maintained in terms of software revisions and protection definitions on the end user computers and mobile devices.
3. The Intelligence Database contains the patterns and signatures which have been identified as known and/or potential threats to the end point. This database is maintained and updated by a dedicated signature developement team to detect and block virus's, malware and other exploits which may put your business at risk.END POINT SECURITY SUMMARY
Why Choose Managed End Point?
The primary reasons for implementing a managed End Point Security solution is to be completely on top of the status of your end devices in terms of protection, attacks and updates.
This is achieved by automating the task of verifiying and monitoring the devices which are authenticated on your network and reporting any descrepancies before they cause your business a problem. Meaning that significantly less manual intervention by IT staff and end users is required during the lifecycle of the end device.
These solutions are often referred to as being driven by artificial intelligence as the software monitoring algorithms are capable of proactively looking at activity between the client computer and the network, then using an analysis engine to determin the threat risk before taking appropirate action to protect the end point.
All of the solutions we provide may be packaged with an off-site backup and recovery solution to provide the ultimate reassurance that your most important assets will be there when you need them.
MANAGING YOUR DATA
What is required to control my data?
With so many open channels of data communication available to your business it is an increasing challenge keeping control of data traffic coming into and leaving your company assets.
This risk of either receiving or sending disruptive, infected or illegal data has grown exponentially over the last 10 years meaning your business needs a reliable method to meet your company policies, processes and procedures. This can be achieved using a combination of traffic control solutions including Email Control, Web Proxy and Firewall platforms. When implemented correctly, these elements offer the ultimate control over email content, web browsing and external intrusion into your companies data assets.
These protection measures may be delivered as an on-site or hosted solution with a variety of management options ranging from unmanaged to fully managed. The choice you make all depends upon the level of in house expertise and time available to manage the solution. Which ever way you decide to go we are here to help ensure you obtain the best value possible from you chosen solution.
We beleive protecting your company's reputation and operational functions are of paramount importance and therefore it is nessesary to carry out a pre-assesment of your requirements.



We conclude your requirements by undertaking a mini Audit of your data communication needs prior to recommending a solution. NTech achieve this by providing a no obligation Audit and mini report to help you decide on how to proceed.
DATA MANAGEMENT SUMMARY
Does my business really need this level of protection?
Without an end to end managed data control suite including all the elements described above there are likely to be gaps in the security of your data. A quick discussion with one of our security specialists will efficiently identify if there are any areas of concern and offer you some options to close those security flaws before they impact your business.



